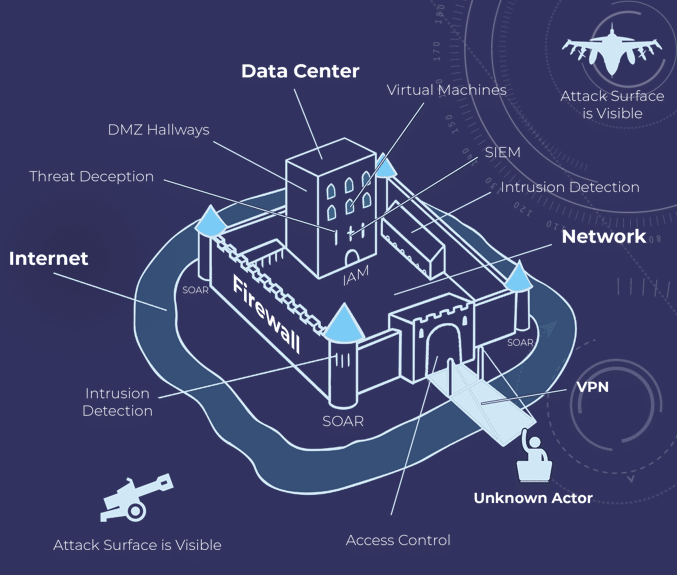
Data breaches exist for roughly 150 days before they are detected. Most companies aim to contain a breach within 30 days. In the first 6 months of 2019 alone, over 4 billion records were exposed in data breaches, and hacked companies are held liable. Worm-enabled malware that targets home-based computers that use corporate VPN connections is on the rise as a way to infiltrate business networks.
In 2020, the U.S. government failed to protect critical and national infrastructure from third-party software creating the most consequential cyber-attack. Worldwide spending on information security and risk management technology and services will continue to grow. Information security spending is expected to exceed $124 billion in 2021.
The use of Aerobyte’s Cyber Defense Framework would have kept each of these examples from happening. Aerobyte’s Cyber Defense Framework identifies breaches instantly and stops them with two clicks. All while likely costing less than the current systems and being timelier and simpler to execute and manage.
TAKE BACK CONTROL OF YOUR COMPANY INFORMATION TODAY